Your choice of external attack surface management software could significantly reduce your data breach risks, but only if it has the proper set of features.
To learn which features to look out for in an external ASM solution, read on.
Learn how UpGuard simplifies Attack Surface Management >
What is the External Attack Surface?
Your external attack surface is the sum of all the potential attack vectors outside your IT network. This includes third-party vendors and even external assets like website domains.
Learn more about the attack surface >
An example of a cyberattack occurring via the external attack surface is the compromise of a third-party solution leading to the compromise of that solution’s users. The most notable real-life example of this in 2023 is the exploitation of the MOVEit Transfer vulnerability. Notorious ransomware gang, Cl0p, exploited a vulnerability in the MOVEit Transfer product, impacting over 95 users, including high-profile customers like US government agencies and Shell.
The external attack surface is typically comprised of three primary layers.
1. Physical Attack Surface
The sum of attack vectors throughout all physical assets and devices inside offices (remote and conventional) and data centers. The physical attack surface is most vulnerable to malicious insider threats, device theft, and baiting (a type of cyberattack where a USB device containing malware is left in an office and unintentionally downloaded onto a computer when plugged in)
Examples of devices typically located within the physical attack surface include:
- Endpoints
- Internet of Things (IoT) devices.
- Shadow IT devices
- Unknown assets of a physical nature.
2. Digital Attack Surface
The digital attack surface is the sum of all security risks and vulnerabilities associated with digital solutions and digital assets. The most popular types of cyberattacks occur in this threat landscape region – data breaches, phishing, ransomware attacks, etc.
Learn the basics of attack surface management >
Some examples of common cyber threats that can be found within the digital attack surface include:
- Internet-Facing Assets – Any digital asset that could potentially be remotely compromised by hackers due to being connected to the internet. Internet-facing assets are commonly compromised through unsecured APIs – the attack vector that led to the Optus data breach.
- Software Vulnerabilities – Security vulnerabilities in digital software and solutions, including SaaS products, that haven’t been patched. Application security exploitation by external threats is one of the primary causes of supply chain attacks.
- Misconfigurations – Software misconfigurations and misconfigured network ports make it easier for hackers to connect to an internet-facing asset. Misconfiguration exploration could lead to man-in-the-middle attacks or a large-scale data breach, like the breach that was avoided when UpGuard security teams found an exposure in Microsoft Power Apps.
Learn about the top misconfigurations causing data breaches >
2. Third-Party Attack Surface
Although a component of the digital attack surface, the third-party attack surface should be placed in its own category since it requires a unique risk management and vulnerability management strategy. The third-party attack surface is exploited with the same attack vectors as the general digital attack surface, except these vectors are associated with third-party services.
This digital footprint region includes:
- Third-Party Vendor Software – Including all third-party vendor SaaS solutions and cloud technology.
- Third-Party Domains – Subsidiary vendor domains and IP addresses associated with vulnerable web servers
- CI/CD Environments – This is a complex attack surface region that includes vulnerable third-party services with access to the resources of your software development architecture.
- Third-Party Integrations with CI/CD Environments – Security risks associated with third-party services with access to sensitive development resources, such as source codes, and are integrated into your CI/CD processes.
Which Layer of the External Attack Surface is Most Critical?
The third-party attack surface is the most critical layer, as it is becoming an increasingly popular target for cyberattacks. During these events, hackers exploit third-party vulnerabilities to either access sensitive information a vendor has been entrusted to process, or compromise a target through a backdoor third-party integration – a common advance technique in supply chain attacks.
Because the cybersecurity standards of third-party vendors tend to fall below best practices, it’s now simpler for cybercriminals to compromise a target through one of its vulnerable third-party vendors instead of contending with its perimeter security controls.
Here are some stats to further highlight the criticality of the third-party attack surface.
- According to the 2022 Cost of a Data Breach report by IBM and the Ponemon Institute, the damage cost of data breaches caused by compromised third parties increased from US$4.33 million to US$4.55 million, which highlights the importance of having an external ASM to mitigate these events.
- Almost 60% of all data breaches are caused by compromised third-party vendors.
- Unsecured external-facing assets account for 12% of data breaches.
Almost 60% of all data breaches are caused by compromised third-party vendors. So by neglecting the third-party attack surface, you’re ignoring the majority of cyber risks responsible for data breaches.
Top 3 Features of External Attack Surface Software
Given the greater criticality of the third-party attack surface above all layers, an ideal external attack surface management tool must be capable of addressing third-party security risks as a focused risk management strategy. However, with digital transformation blurring the divide between internal and external attack surfaces, ASM tools must be equally capable of addressing internal attack surfaces, all from a single centralized platform.
Having a single tool for managing internal and external attack surfaces will avoid the irony of unnecessarily expanding your attack surface with solutions designed to minimize it.
The following features include key ASM capabilities addressing internal and third-party attack surface requirements for preventing first-party and third-party data breaches.
1. Attack Surface Reduction
The larger your attack surface, the greater your data breach risks. An ideal external ASM tool should assist in identifying unnecessary attack surface regions that should be eradicated. This process involves asset discovery (see the following section) and attack surface monitoring to produce reduction insights prioritizing the most critical attack surface regions.
Watch the video below for an overview of the attack surface reduction process using the UpGuard platform.
Request a free trial of UpGuard >
2. Asset Discovery
Asset discovery is arguably one of the most challenging components of attack surface management. Keeping an accurate inventory of your current digital assets is hard enough, but with domains and IP addresses constantly being added to your internal and third-party attack surface, security teams are perpetually lagging behind their expanding attack surfaces, which severely limits their data breach risk awareness.
An ASM solution must be capable of rapidly identifying all the assets in your digital footprint, including domains, IP addresses, web servers, and third- and fourth-party vendors.
You cannot secure what you cannot see. Attack surface blind spots are essentially data breaches waiting to happen.
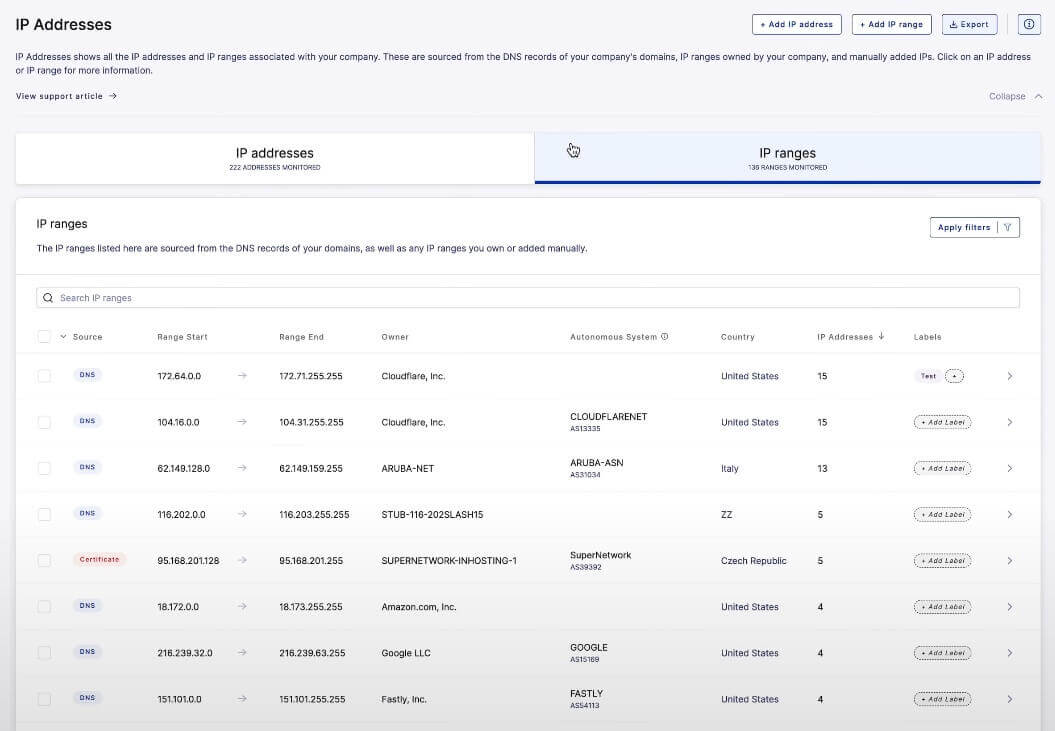
Request a free trial of UpGuard >
3. Vendor Risk Management Integration
Because third-party attack surface management is a function of vendor risk detection and evaluation, an external ASM solution should be integrated with a complete Vendor Risk Management tool. Ideally, the two cybersecurity programs should be offered in a single platform to keep the internal attack surface minimal.
The following VRM program features provide sufficient vendor risk exposure context to support effective third-party attack surface management.
Risk Assessment Management
Vendor risk assessments identify poor security patching practices and other software security risks increasing third-party breach susceptibility. Because this workflow commonly causes disruptions in downstream risk management practices, choose a solution that can automate the vendor risk assessment process.
Watch the video below to learn how UpGuard streamlines risk assessment workflows.
Risk Remediation Management
Knowing the impact of remediation efforts on security postures will help you determine whether incident responses have reduced vendor risk exposures.
Watch the video below to learn how UpGuard simplifies risk remediation workflows.
Learn the key features of effective risk remediation software >
Dashboards
Dashboards summarizing vendor risk exposure offer a single-pane-of-glass view of your entire third-party attack surface. With continuous monitoring of third-party attack surfaces, these dashboards can help you track security posture improvements in real-time.

Learn about UpGuard’s dashboard and reporting features >
Security ratings
Security ratings offer an objective and unbiased evaluation of a vendor’s security posture. Because security ratings are very good at providing a snapshot of a vendor’s cybersecurity performance, according to Gartnerthis feature will become as important as credit ratings when assessing the risk of existing and new business relationships.

Learn about UpGuard’s security rating feature >
With the ability to instantly understand each vendor’s data breach susceptibility, security ratings make it possible to represent your third-party risk exposure in the form of a threat matrix, helping you instantly identify the most critical regions of your third-party attack surface.

