QNAP Systems, Inc. Is a Taiwanese company specializing in networked storage equipment for applications such as file sharing, virtualization, storage management and tracking.
What happened?
DeadBolt ransomware encrypts QNAP NAS systems around the world, claiming that they exploit zero-day vulnerabilities in the device’s firmware to do so.
When the attacks began, QNAP clients discovered that their files had been encrypted and that their file names had been added with the .dolbolt file extension.
#QNAP There seems to be something new Heresy attack: #smuggler. What’s the fix, QNAP?
Every customer is asked to pay 0.03 #BTC pic.twitter.com/1XS1liTZn2– Wireless-News (@news_wireless) January 25, 2022
The QNAP device login page has been hijacked, and a message reading “Warning: Your files have been locked by DeadBolt” is displayed instead of ransom notes that will be placed in any folder on the device.
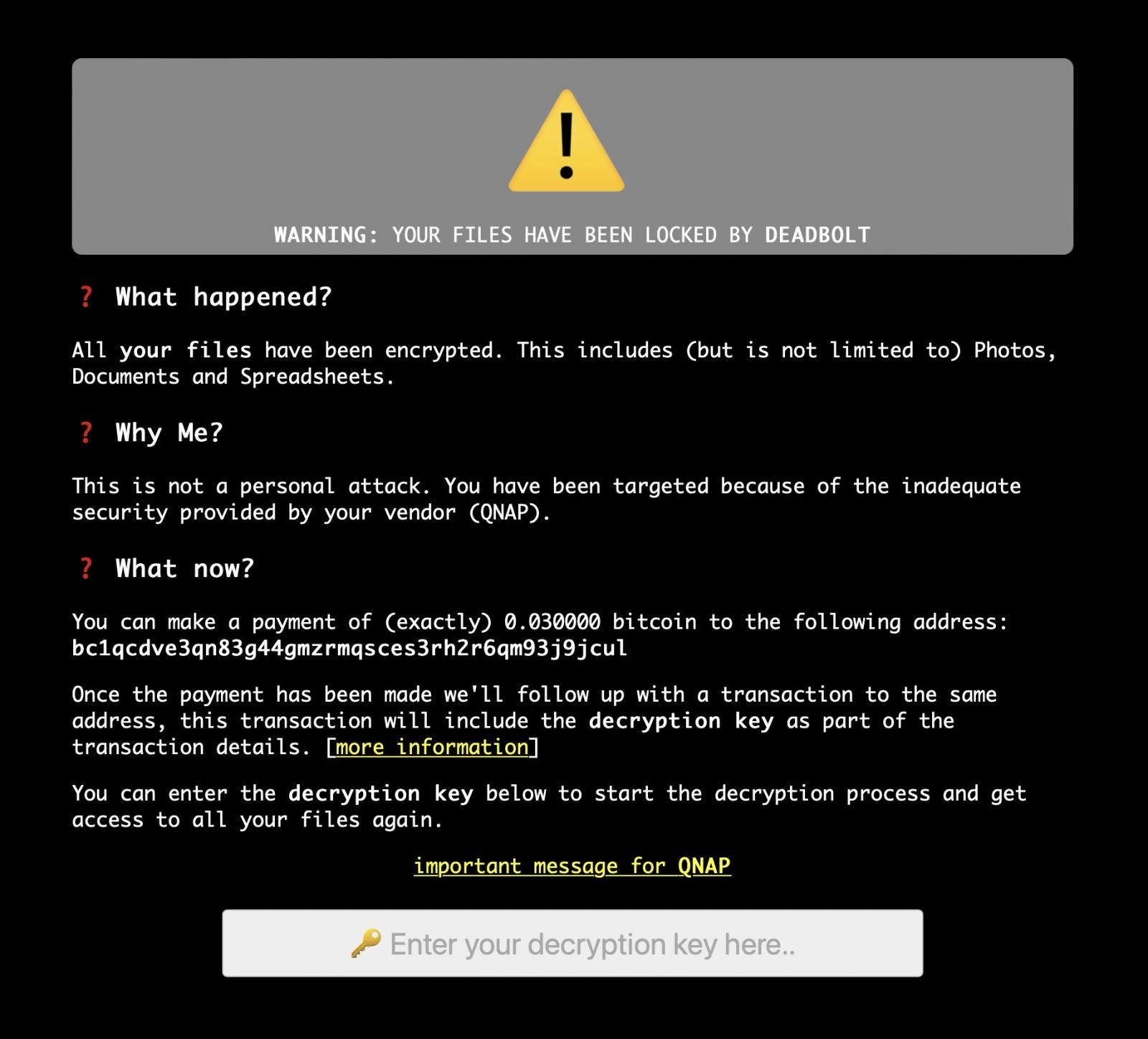
as BleepingComputer The page reports that the page advises the victim to send 0.03 Bitcoin (about $ 1,100) to the unique Bitcoin address for each victim, indicated in the message.
Following receipt of the compensation, the threat agents say they will make a follow-up transaction to the same address that will contain the decryption key, which can be obtained by following the steps outlined in this document.
You can then type this decryption key on the device screen to enable decoding of the files on the device. Currently, there is no guarantee that paying a ransom will result in the delivery of a decryption key, or that customers will be able to decrypt their data after doing so.
Because the threat players claim that the attack is carried out through zero-day vulnerability, it is highly recommended that all QNAP customers disconnect their devices from the Internet and put them behind a firewall as soon as possible.
A message for QNAP can be found on the main ransom note page, and clicking on it will bring up a message from the DeadBolt gang that is exclusively tailored for QNAP and its customers.
Make a 50 BTC bitcoin payment to bc1qnju697uc83w5u3ykw7luujzupfyf82t6trlnd8.
You will receive a universal decryption master key (and instructions) that can be used to open all your customers in their files. In addition, we will also send you all the details about the zero-day vulnerability to security@qnap.com.
How can Heimdal ™ help?
Ransomware is one of the most common and serious cyber threats today, with generally dangerous consequences. Learning how to avoid this should be a top priority for any business concerned with the safety of its employees, customers, partners, assets, money and business processes.
In the fight against ransomware, Heimdal Security provides its customers with an exceptional integrated cyber security package that includes the Ransomware encryption protection A module, universally compatible with any antivirus solution and completely unsigned, that ensures excellent detection and repair of any type of ransomware, whether file-free or file-based (including the latest ones like LockFile).
If you liked this article, follow us LinkedIn, Twitter, Facebook, YouTubeAnd Instagram For more news and topics on cyber security.
