Few Indian businesses are included in the ever-increasing list of major data breaches. But data suggests that this streak of luck could soon be reaching its end.
Increasing third-party security risks and a deficiency of security controls addressing them create the perfect conditions for a large-scale global supply chain attack facilitated by breached Indian business.
To avoid being used as an attack vector, Indian businesses must urgently increase their third-party security posture with a resilient Vendor Risk Management Program.
To learn about the concerning developments in India’s third-party threat landscape, and the importance of a VRM program to address them, read on.
What is Vendor Risk Management?
A Vendor Risk Management (VRM) program aims to mitigate negative business impacts, specifically in the category of cybersecurity risks. This is achieved through the identification, management, and ongoing monitoring of third-party security risks to decrease the potential of any vendor becoming an attack vector in a data breach campaign.
Vendor risk management differs from Third-Party Risk Management (TPRM) in its explicit focus on mitigating third-party security risks. A TPRM program covers the complete scope of risks to business continuity, of which vendor risk management is a subset.
Learn more about Vendor Risk Management.
Vendor Risk Management is important because it allows Indian businesses to leverage the increased operational efficiencies made possible through vendor relationships without the detrimental impacts of their unavoidable security risks.
There are security risks associated with every vendor, and when onboarded, their attack surface combines with your own, making their security risks your security risks.
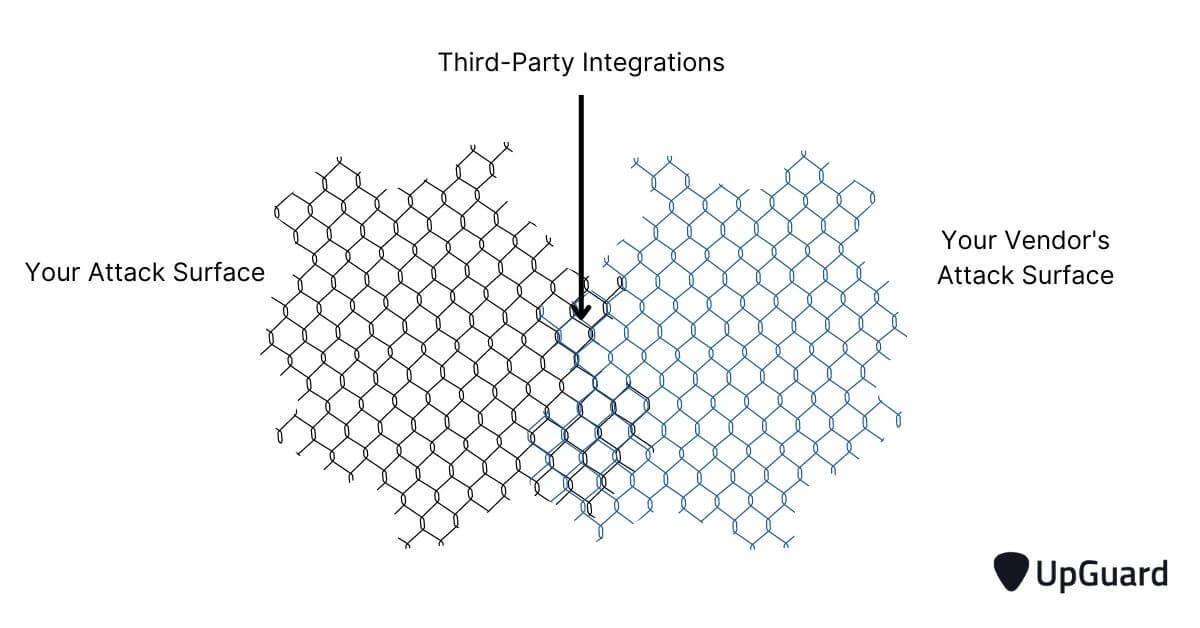
A Vendor Risk Management program ensures a vendor’s residual and inherent risks do not exceed your defined risk appetite, either during the onboarding process or throughout the lifetime of their relationship.
Learn more about defining your risk appetite.

By introducing additional security risks, vendor relationships also increase the potential of a more sinister cyber threat – supply chain attacks.
During a supply chain attack, a target is compromised by exploiting a security vulnerability of a vendor in its supply chain. This ‘backdoor’ approach makes the cyberattack pathway easier, giving cybercriminals the option of contending with a vendor’s often less sophisticated security efforts instead of the more complex security controls protecting a victim’s IT boundary.
Learn more about supply chain attacks.
Vendor Risk Management involves identifying, remediating, and monitoring third-party risks. These processes contribute to an overarching effort of giving business owners visibility and control over their entire third-party attack surface, thereby reducing the impact of all third-party cyberattacks, including supply chain attacks.
5 Reasons Why a Vendor Risk Management Program is Important for Indian Organizations
If you own or operate a business in India, you need to be aware of these critical third-party security trends highlighting the importance of implementing a Vendor Risk Management Program.
1. The Cost of a Data Breach in India is Increasing
Since 2020, the average data breach cost in India has continued to rise, with 2022 setting a new record high.
According to the annual Cost of a Data Breach Report by IBM and the Ponemon Institute, the average cost of a data breach in India in 2022 is approximately 18.5 Crores (US$ 2.32 million). This value has risen by an astonishing 15% since 2019.
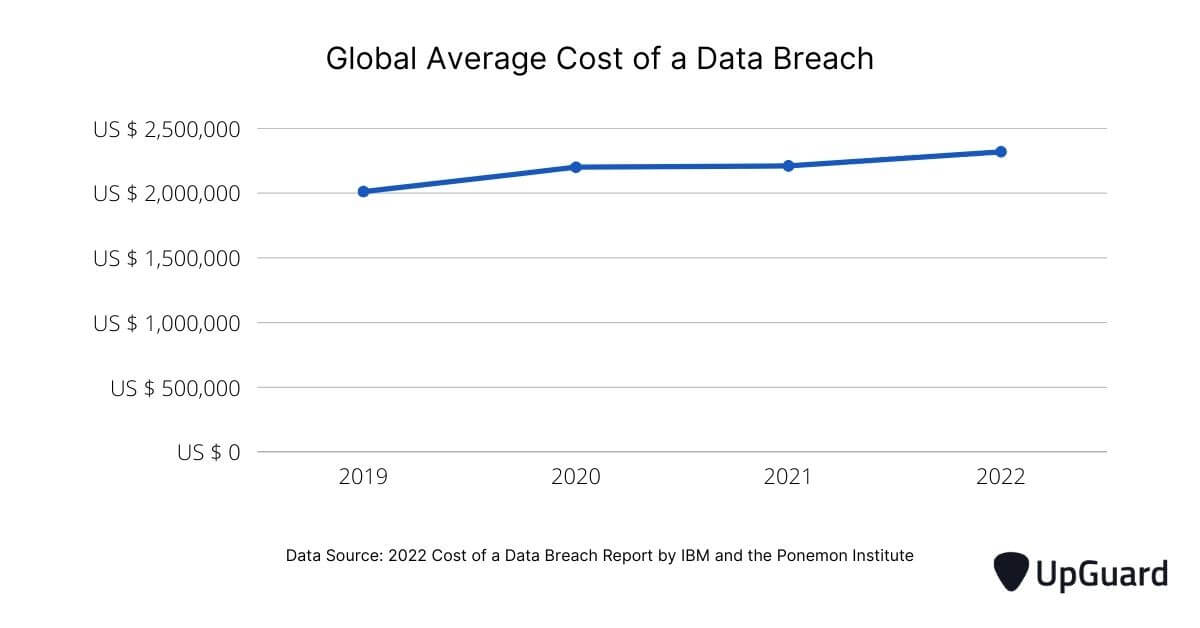
The 2022 Cost of a Data Breach report also ranked India as the fourteenth most expensive country to experience a data breach.
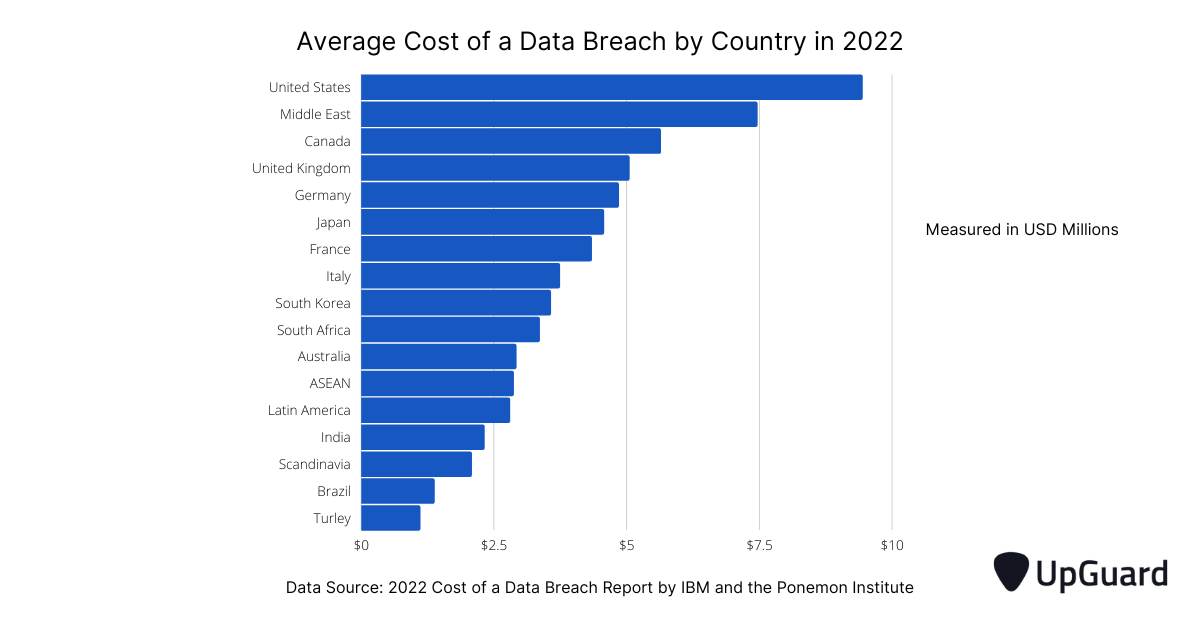
As impactful as these trends may seem, they still fail to represent the actual severity of data breach damages in India. The same report estimates the data breach damage costs for the United States at US $4.35 million, which is 88% larger than India’s estimate.
Compared to the United States, India’s damage costs seem almost insignificant. But a more accurate analysis would need to consider differences in the cost of living between the two countries, a discrepancy that can be quantified through the Purchasing Power Parity system.
The Purchasing Power Parity (PPP) is an index comparing the absolute purchasing power of each country relative to the United States.

According to 2021 estimates, India’s Purchasing Power Parity is 23.138 times larger than the United States. With this conversion rate, a data breach damage cost of 18.5 Crores in India would equate to 63.78 Crores (or about US$ 8 million) in damages in the United States – 84% more than the 2022 damage cost estimate for the United States.
With a more equitable cost analysis, India should actually be ranked as one of the most expensive countries to experience a data breach, a statistic that every business owner in India should find very concerning.
India’s sensitivity to data breach damages extends to the third-party threat landscape, highlighting the criticality of a vendor risk management solution to increase third-party breach resilience.
2. Vulnerabilities in Third-Party Vendor Software Ranked Third Most Costly Attack Vector in 2022
In 2022, vulnerabilities in third-party software are ranked the third most expensive initial attack vector leading to a data breach.

The associated damage cost for this attack vector has increased in the past year by over 175 Lakh.

This data reveals that cyber attackers are increasingly preferring third-party vulnerabilities in data breach campaigns for their more significant damage potential.
A resilient risk management solution needs to reduce risk exposures for all six attack vectors that have increased in cost in the last year. Since third-party risks are included in this set, such a solution needs to include a Vendor Risk Management program.
3. Supply Chain Attacks are Increasing
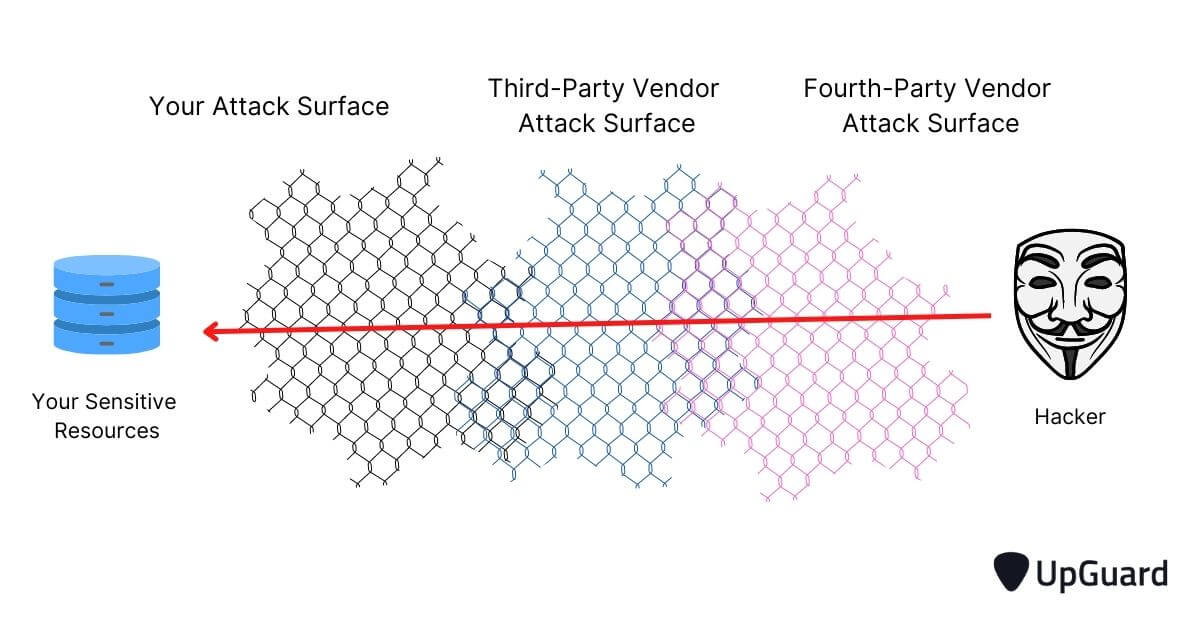
Because the threat landscapes of your service providers blend with your own after onboarding, every vendor becomes a potentially exploitable pathway to your sensitive resources, making each service provider a potentially exploitable pathway to your sensitive resources.
Because digital transformation also combines the attack surfaces of service providers and their clients, a breach involving a fourth party could also lead to your sensitive data being compromised.
An increase in data breaches caused by compromised third-party vendors (supply chain attacks) is an expected outcome of the rising third-party vulnerabilities damage cost trend observed in item two above.

Because the frequency, impact, and cost of supply chain attacks are increasing, outsourcing business operations to service providers is now a matter of information security requiring vendor due diligence and third-party risk mitigation processes.
4. Many Popular Third-Party Vendors Based in India
Rising supply chain attack events and costs impact two classes of businesses.
- Entities sourcing partnerships with third-party vendors – because they’re at risk of being breached through a supply chain attack.
- Service providers – because they’re at risk of becoming initial attack vectors in a supply chain attack.
Service providers have greater cause for concern. A single third-party vendor typically services a vast client network so that a single breach could lead attackers to a treasure-trove of sensitive data for multiple SMEs and Fortune 500 businesses.

Because a single breach could lead to multiple victims, the increased profitability of this style of attack makes service providers a high-risk target. This is unfortunate news for India since the country is home to many popular third-party vendors with a global client network.
5. India is Leading the World in Supply Chain Processes, Making them a Prime Target for Supply Chain Attacks
In July 2022, India, in partnership with 17 other economies, including the US and the European Union, outlined a roadmap for establishing a resilient global supply chain. Even before this partnership agreement, the world started taking notice of India’s improving supply chain management efforts.
According to Forbes, the Mumbai-based company, Asian Paints, set an exemplary standard of resistance and adaptability in its supply chain processes during the pandemic. While most businesses experienced a heavy blow to their bottom line from supply chain constraints, Asian Paints’ adaptable model not only allowed them to remain profitable during the most tumultuous COVID-19 period but also created additional business opportunities.
But the outcomes of India’s fast-developing supply chain management skills aren’t all positive.
India shines as a beacon of light in a struggling global economy. A growing number of prosperous organizations globally will likely begin to prefer India’s third-party services for its more affordable prices. This means, in the coming months, more Indian technology companies will have access to high-profile, sensitive resources through third-party relationships, increasing the country’s overall likelihood of supply chain attacks.
In a struggling global economy, India is a beacon of light, offering high-quality third-party tech solutions at affordable prices.
Even if an Indian third-party service provider to a high-profile entity has effective data breach security controls in place, if they have a service provider with a poor security posture, a successful supply chain attack could still occur through this fourth-party relationship .
Learn more about fourth-party risk.
UpGuard Helps Indian Businesses Implement an Effective Vendor Risk Management Program
UpGuard helps Indian businesses mitigate the impact of data breaches and supply chain attacks with a platform addressing the complete scope of Vendor Risk Management.
- Continuous attack surface monitoring – Monitor internal and third-party attack surfaces for emerging security risks and security posture changes in real-time.
- Track vendor performance – Track the key security metrics of all your vendors to discover behaviors increasing the likelihood of third-party breaches.
- Manage vendor risk assessments – Quickly select relevant questionnaires from an extensive library, or create your own custom questionnaire for highly-targeted security threat analysis. You can also map assessment responses to applicable regulations to discover regulatory compliance gaps.
- Data leak management – Discover and shut down internal and third-party vendor data leaks before they’re exploited by cybercriminals.
Click here to try UpGuard for free for 7 days.
